When we last left off, I had spent an excess of 100 hours (I’m not exaggerating since that entire time I was working, I listened to This American Life and went through over a hundred one-hour episodes) soldering and tinkering with the Vita logic board to try to dump the eMMC. I said I was going to buy a eMMC socket from taobao (the socket would have let me clamp a eMMC chip down while pins stick out, allowing the pressure to create a connection) however, I found out that all the sellers of the eMMC socket from taobao don’t ship to the USA and American retailers sell the sockets for $300 (cheapest I could find). So I took another approach.
Packet Sniffing
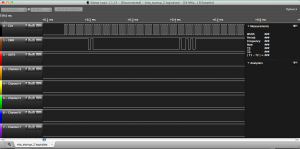
My first hypothesis on why it is not working is that there’s some special initialization command that the eMMC requires. For example, CMD42 of the MMC protocol allows password protection on the chip. Another possibility was that the chip resets into boot mode, which the SD card reader doesn’t understand. To clear any doubts, I connected CLK, CMD, and DAT0 to my Saleae Logic clone I got from eBay.
Vita eMMC points connected to logic analyzer.
As you can see from the setup, I had the right controller board attached so I can get a power indicator light (not required, but useful). I also took the power button out of the case and attached it directly. The battery must be attached for the Vita to turn on. Everything is Scotch-taped to the table so it won’t move around. Once all that is done, I captured the Vita’s eMMC traffic on startup.
First command sent to eMMC on startup
After reading the 200 paged specifications on eMMC, I understood the protocol and knew what I was looking at. The very first command sent to the Vita is CMD0 with argument 0x00000000 (GO_IDLE_STATE). This is significant for two reasons. First, we know that the Vita does NOT use the eMMC’s boot features. The Vita does not have its first stage bootloader on the eMMC, and boots either from (most likely) an on-chip ROM or (much less likely) some other chip (that mystery chip on the other side maybe?). Second, it means that there’s no trickery; the eMMC is placed directly into Idle mode, which is what SD cards go into when they are inserted into a computer. This also means that the first data read from the eMMC is in the user partition (not boot partition), so the second or third stage loader must be in the user partition of the eMMC. For the unfamiliar, the user partition is the “normal” data that you can see at any point while the boot partition is a special partition only exposed in boot mode (and AFAIK, not supported by any USB SD card reader). Because I don’t see the boot partition used, I never bothered to try to dump it.
Dumping
I tried a dozen times last week on two separate Vita logic boards trying to dump the NAND with no luck. Now that I’m on my third (and final) Vita, I decided to try something different. First, I did not remove the resistors sitting between the SoC and eMMC this time. This is because I wanted to capture the traffic (see above) and also because I am much better at soldering now and the tiny points doesn’t scare me anymore. Second, because of my better understanding of the MMC protocol (from the 200 page manual I read), I no longer attempted to solder DAT1-DAT3 because that takes more time and gives more chance of error due to bad connections. I only connected CLK, CMD, and DAT0. I know that on startup, the eMMC is placed automatically into 1-bit read mode and must be switched to 4-bit (DAT0-DAT3) or 8-bit (DAT0-DAT7) read mode after initialization. My hypothesis is that there must be an SD card reader that followed the specification’s recommendation and dynamically choose the bus width based on how many wires can be read correctly (I also guessed that most readers don’t do this because SD cards always have four data pins). To test this, I took a working SD card, and insulated the pins for DAT1-DAT3 with tape. I had three SD card readers and the third one worked! I know that that reader can operate in 1-bit mode, so I took it apart and connected it to the Vita (CLK, CMD, DAT0, and ground).
As you can see, more tape was used to secure the reader.
I plugged it into the computer and… nothing. I also see that the LED read indicator on the reader was not on and a multimeter shows that the reader was not outputting any power either. That’s weird. I then put a working SD card in and the LED light turned on. I had an idea. I took the SD card and insulated every pin except Vdd and Vss/GND (taped over every pin) and inserted the SD card into the reader. The LED light came on. I guess there’s an internal switch that gets turned on when it detects a card is inserted because it tries to draw power (I’m not hooking up Vdd/Vss to the Vita because that’s more wires and I needed a 1.8V source for the controller and it’s just a lot of mess; I’m using the Vita’s own voltage source to power the eMMC). I then turned on the Vita, and from the flashing LED read light, I knew it was successful.
LED is on and eMMC is being read
Analyzing the NAND
Here’s what OSX has to say about the eMMC:
Product ID: 0x4082 Vendor ID: 0x1e3d (Chipsbrand Technologies (HK) Co., Limited) Version: 1.00 Serial Number: 013244704081 Speed: Up to 480 Mb/sec Manufacturer: ChipsBnk Location ID: 0x1d110000 / 6 Current Available (mA): 500 Current Required (mA): 100 Capacity: 3.78 GB (3,779,067,904 bytes) Removable Media: Yes Detachable Drive: Yes BSD Name: disk2 Partition Map Type: Unknown S.M.A.R.T. status: Not Supported
I used good-old “dd” to copy the entire /dev/rdisk2 to a file. It took around one and a half hours to read (1-bit mode is very slow) the entire eMMC. I opened it up in a hex editor and as expected the NAND is completely encrypted. To verify, I ran a histogram on the dump and got the following result: 78.683% byte 0xFF and almost exactly 00.084% for every other byte. 0xFF blocks indicate free space and such an even distribution of all the other bytes means that the file system is completely encrypted. For good measure, I also ran “strings” on it and could not find any readable text. If we assume that there’s a 78.600% free space on the NAND (given 0xFF indicates free space and we have an even distribution of encrypted bytes in non-free space), that means that 808.70MB of the NAND is used. That’s a pretty hefty operating system in comparison to PSP’s 21MB flash0.
What’s Next
It wasn’t a surprise that the eMMC is completely encrypted. That’s what everyone suspected for a while. What would have been surprising is if it WASN’T encrypted, and that tiny hope was what fueled this project. We now know for a fact that modifying the NAND is not a viable way to hack the device, and it’s always good to know something for sure. For me, I learned a great deal about hardware and soldering and interfaces, so on my free time, I’ll be looking into other things like the video output, the mystery connector, the memory card, and the game cards. I’ve also sent the SoC and the two eMMC chips I removed to someone for decapping, so we’ll see how that goes once the process is done. Meanwhile, I’ll also work more with software and try some ideas I picked up from the WiiU 30C3 talk. Thanks again to everyone who contributed and helped fund this project!
Accounting
In the sprit of openness, here’s all the money I’ve received and spent in the duration of this hardware hacking project:
Collected: $110 WePay, $327.87 PayPal, and 0.1BTC
Assets
Logic Analyzer: $7.85 Broken Vita logic board: $15.95 VitaTV x 2 (another for a respected hacker): $211.82 Rework station: $80 Broken 3G Vita: $31 Shipping for Chips to be decapped: $1.86
Total: $348.48 (I estimated/asked for $380)
I said I will donate the remaining money to EFF. I exchanged the 0.1BTC to USD and am waiting for mtgox to verify my account so I can withdraw it. $70 of donations will not be given to the EFF by the request of the donor(s). I donated $25 to the EFF on January 10, 2014, 9:52 pm and will donate the 0.1BTC when mtgox verifies my account (this was before I knew that EFF takes BTC directly).



Great work..I loo forward to the video out review.
Congratz Yifanlu, thanks for taking time doing this!!
Thank’s Yifan Lu, Very informative post. wooow spending 100h work :D. You are the best. wish you good luck. the comparaison you made between the psp flash0=21mb and the about 20% of vita nand = 808.70 !! so it is 38.6 times psp’s power !!! That’s really “hefty” !!
Very fascinating read. Well done for the effort, and you’re right; it’s important we knew whether it was a viable way of hacking it.
Thank you very much for your time-donation to the comunity :D
Nice! We can safely assume the eMMC uses per Vita unique keys, likely AES. What would perhaps be interesting as well is to see what happens next after the Go Idle command. Those commands itself would not be encrypted, right?
The commands after the go idle are more normal commands for reading emmc. There’s no such thing as a encrypted command.
[…] Source: Yifan’s blog […]
Good work man… my respect 4 u….
You have done great. My hats off to you. Keep up the good work. I’m sure in time we will find a way. Your time and efforts are very appreciated by the community, I am sure of it!!!!
Do you mind posting dump image?
It will provide people without the hardware to take a look at the contents of the dump. I know that’s ‘useless’ since it’s encrypted. But, it’s still worth a shot.
It is useless. I can assure you of that. If you’re curious, you can do dd if=/dev/urandom of=dump.img bs=1MiB count=3800
great work and very respectful. Very nice to put the budget.
If you ever need to order from taobao you can use an agent such as bhiner to buy it for you and ship it. I got a 4k TV with them, it took a month to get here due to shipping but the service was good. http://www.bhiner.com/
[…] desarrollador Yifan Lu ha anunciado que ha conseguido dumpear la memoria NAND de PS Vita, la última portátil de […]
Thank you very much for Yifan Lu :D Dump 2.12 wifi vita http://i.hizliresim.com/xYMrv2.jpg
[…] No mais, para quem quiser acompanhar o passo a passo do processo além de diversas outras informações relacionadas ao hardware do vita, confira o blog do Yifan. […]
[…] capiti meglio probabilmente solo con un eventuale decriptazione di quei 3.78GB Vi lascio al link del blog dell'autore del dump, dove egli spiega tutto il processo che ha fatto per effettuare il dump, […]
this might sound silly, but if you could find a psvita (faulty or working) on an firmware below 1.50 could you use the psp master key to decrypt the nand? assuming thats whats protecting the information from being read
Nope, unfortunately your assumption is wrong. Even before 1.50, you can’t decrypt anything. We can’t decrypt anything on the vita. Period. (There’s rumors of beta packages being decryptable but I haven’t seen solid evidence)
thats unfortuanate :( thanks for all your hard work, the fact that you learned how to pull the nand in such a short period of time is inspiring
Hey Lu, great work. The 100h was worth it since you learned quite a lot in the process. Just wanted to throw a quick bone at you: For the mistery port, many fellows suspect a service port of some kind, if not, it can also be used as an accessory port if I remember right, it provides power. As you may already know, there are addons that provide video out by using a capture card (internal) and a PC with the decoding software. Many say that the capture card follows the same principle as the 3ds capture card and so look out for a chip that takes care of encoding and conversion on the PSVita.
Anyways, that’s all I have for now, please let me know if it is of any use, I can find out more if not. Good luck and thank you very much for sharing. P.S.: I have a slim PSVita as well (OG is 3g) if you need to look at any board revisions (not sure if ifixit took it apart) to look at.
Thanks I know how the vita capture mod works. It uses the test pads for the video signals going to the oled display and uses a fpga chip to decode it. The mystery port has no video signals but I think it may be USB otg
I don’t understand, where the nand is decrypted ? In the CPU ? Have it a “boot part” in the firmware to see how it is decrypted ? Sorry if my english is bad.
It is most likely decrypted in memory by the CPU whenever a block is read. On boot, there’s an on chip bootrom that loads.
You’ve done some amazing work Yifan Lu, and I can barely imagine how amazing it must have felt once the card reader led turned on and the nand dump started.Cheers and keep up the good work.
Well yifan this might help us but unless we collect a 11000$ funds http://chipworks.force.com/catalog/ProductDetails?sku=SON-CXD5315GG&viewState=DetailView
No, it won’t really help. It’s not detailed enough to allow us to decode any roms.
According to achivements on Vita hacking is threatened any chance that Vita will be hacked in 2014?
Sorry. Threatened was typo Threatened =there
[…] desarrollador Yifan Lu ha anunciado que ha conseguido dumpear la memoria NAND de PS Vita, la última portátil de […]
I wish the vita to be hacked just enough for people to create a homebrew similar to remotejoy lite. I wish pray AND hope this happens since Sony doesn’t care enough to create a vita with HDMI output. :’(
I think one part on NAND is used to store downloaded pkg, cause in PS3 we need 2 x the size of the package we downloading (download and installation) but not on PSVita, its seem to be the package is stored in reserved area for downloading and after decompressed on the memcard.
Awesome work man! Btw, where you got that Vita for $31? :D
eBay. Broken screen.
hi yifan can u send me hdmi soldering points and other details Plz.
Yifan, is it possible to do a live memory dump? Scan the traces or onboard memory while its being read/outputted and dump the information to a file?
Nope. Memory is embedded on the same chip as the CPU. No traces afaik. Maybe there’s a debug output on the board but that’s unlikely.
Sure that’s a good place to start. Who has the tools and skills to fabricate a breakout board for the vita CPU though?
So the only reasonable way of going about this is software wise, hoping Sony slips up somewhere and allows us minor access to say a decrypted memory card.
If feasible, write or are not sure?
merci y fan lu bon courage j’espér que tu réussite ton travail pour perte ps vita
Gjbu! Good Job!.
“As you can see from the setup, I had the right controller board attached so I can get a power indicator light (not required, but useful).”
Left board where the dpad is…?
Hi can we swap an Emmc from board FW 3.60 to other one FW 3.65 as a way to downgrade?